When there is a network there is bound to be network related issues too and the most common of all the problems are the ones concerning the security of network infrastructure. One of these security issues, is the ddos or Distributed Denial of Service. In this a number of systems are compromised of the security by a virus and a single target is attacked and ultimately forced to shut down. DDOS attack is a common fear factor for enterprise network managers. When a number of systems are hacked with a virus and the security is compromised, the target system is attacked with several messages which cannot be controlled by the user’s end. Hence the system shuts down and the user will be unable to access the network.
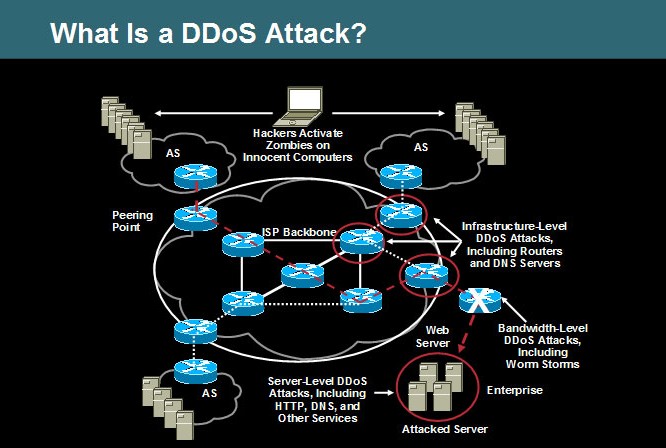
What Happens in DDOS attack?
In a ddos attack the attacker starts taking advantage of the vulnerability in the security of a particular system and uses it to enter other systems. In ddos there can be two types of attacks. One attack can be targeted towards a certain network and the other type of attack takes place on a particular application. In the first attack the target is a network and in the second is the application wherein the service or database is overloaded with application calls. This causes denial of service. In a ddos attack the computer which is attacked is called the “bot”. In ddos there is breakage of several devices through the internet. This results in tiredness of bandwidth, community bunch sources and hub processing capacity and many other things.
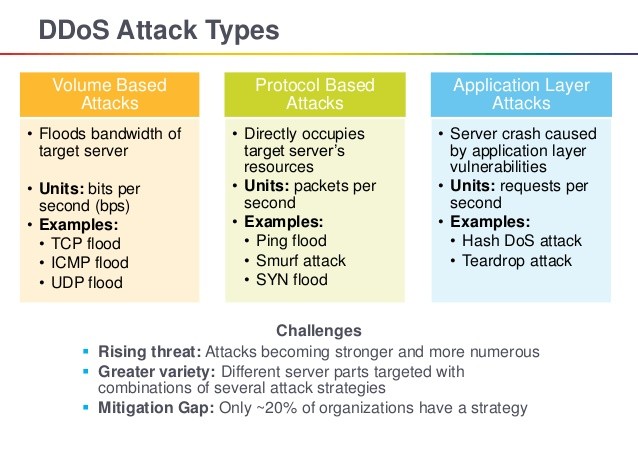
Types of DDOS attack
- Application Layer Attacks- If you are using windows or Open BSD, your servers can be at a risk of ddos attack. The goal of this kind of attack is to bombard the server with innocuous requests which will crash the server and prevent the legit users from the website access, online service etc. This impacts the business of a company hugely. With the business down for even few minutes a company’s revenue and reputation can be damaged significantly.
- Protocol Attacks- The ddos attacks eat up several resources and stop hardware, software or users from communicating with that server. Some common examples of this kind of attacks are SYN floods, Smurf ddos, ping of death.
- Volume Based Attacks- This kind of attacks include UDP floods, ICMP floods and other kinds of network flooding with spoofed packets. The goal of this attack is to saturate the network’s bandwidth, as a result legitimate traffic and data is prevented from getting through.
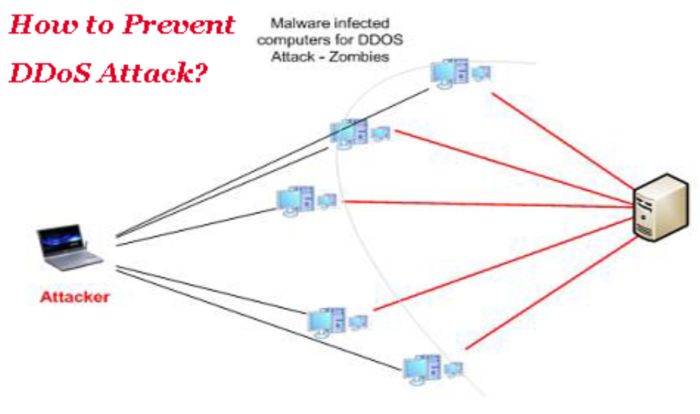
How to prevent DDOS attack?
Stopping DDos attacks requires preparation. If you are not prepared for the attack you will be knocked over. You must take steps to increase resiliency and availability. The best and up to date practices for the network infrastructure and DNS must be used. A high performance perimeter defense system must be used. This will mitigate risk and keep the online resources and internal network working perfectly without risk of suspension and interruption. Indentifying DDOS attack early will provide the best chance of taking necessary action. Configure your routers to increase your system security level. Set traffic limits, filters on the router to prevent network or servers overwhelming and to detect malicious packets. Set up VPNs and trusted network connections.
There are many defense technologies available to detect and prevent ddos attacks. Use these technologies to protect your network.